To sign up for our daily email newsletter, CLICK HERE
Many companies are nowadays depending on the cloud – either migrating to the cloud entirely or depending on cloud-based solutions for important internal company processes. Either way, cloud and container software are indispensable tools for many modern companies.
However, as with any digital tool, especially ones that involve employee information and private data, security is always a major concern. A company must secure and monitor its cloud and container software for vulnerabilities.
While modern security software quite effectively protects vital information and assets from falling into the wrong hands, cybercrime is still a major problem. Finding the right security software for your cloud and containerized environments significantly reduces the risk of disastrous breaches.
Best Practices To Keep Your Cloud and Container Safe
Securing your cloud infrastructure and container environments is crucial to protect your data, applications, and resources from cyber threats. Here are some best practices to help you keep your cloud and containers safe:
- Choose a secure cloud provider – Start by selecting strong cloud security solutions such as a cloud server provider that offers vast security features and compliance certifications.
- Implement strong authentication and access control – Use multi-factor authentication for user and admin access, as well as limited access for each user with the principle of least privilege (PoLP).
- Enforce IAM policies – Define and enforce identity and access management (IAM) policies to control who can access your cloud resources and what actions they can perform.
- Take encryption of data seriously – Use encryption to protect the data stored in the database (data at rest) and the data while transmitted (data in transit). If your cloud provider doesn’t provide built-in encryption services, opt for strong encryption compatible with your cloud solution.
- Employ security scanning tools – Invest in the security tools to check container images for vulnerabilities before deployment.

- Use Kubernetes namespaces – Isolate containers using Kubernetes namespaces, and use Kubernetes monitoring practices to identify performance issues in a timely manner.
- Employ container orchestration security – If using container orchestration tools like Kubernetes, secure the control plane with RBAC (Role-Based Access Control) and implement network policies.
- Stay up to date – Keep your cloud instances and container images up-to-date with the latest security patches and updates. Regularly update Kubernetes and its components for security patches.
- Configure network security – Your network security groups and firewalls need configuring to control incoming and outgoing traffic to your cloud resources. You can further segment your cloud resources with Virtual Private Cloud (VPC) or Virtual Networks.
- Back up, back up, back up – Backing up your data regularly is an essential security measure, although it doesn’t hurt to mention it once more. Implement automated data backup and recovery processes to ensure data can be restored in case of an incident.
- Educate your team – Ensure that your team is aware of security best practices and conducts regular training and awareness programs.

- Invest in security testing – Set up a team to conduct regular security assessments, penetration testing, and vulnerability scanning to identify and remediate weaknesses.
- Improve DevOps security practices – Integrate security into your DevOps pipeline by using Infrastructure as Code (IaC) and Security as Code (SaC) practices.
- Comply with industry regulations – Understand the compliance requirements relevant to your industry and ensure your cloud and container environment complies with these regulations.
- Create an incident response plan – Develop an incident response plan to quickly address and recover from security incidents. Test and refine this plan regularly.
- Reinforce SPF records – Use SPF (Sender Policy Framework) to authorize only trusted servers to send emails on your behalf. Use an SPF record check software to gain full control over the server’s access.
- Invest in CSPM tools – Consider using CSPM (Cloud Security Posture Management) tools to continuously assess and improve your cloud security posture.
- Monitor and audit activity – Implement logging and monitoring solutions to track and analyze activities within your cloud environment and containers. Set up automated alerts for suspicious or unauthorized activities.
- Vendor security best practices – Follow the best practices recommended by your cloud service provider. Cloud providers often publish security guidelines and whitepapers.
Remember that security is an ongoing process, and it requires vigilance and regular updates to adapt to evolving threats. Hackers become more innovative and creative every day, which is why you need to be on top of the game at all times.
To make sure your security is maintaining the highest standards, dedicate security testing personnel to follow the protocols and challenge cloud and container security.
When it comes to ensuring the safety of the software you produce, you should consider hiring a quality assurance specialist, experienced to cover all aspects of the software, including the security measures involved.
8 Tools For Cloud and Container Security
Here’s a list of 8 applications that can keep your cloud and container safe from unwanted intrusions regardless of what industry you work in, be it SaaS, fintech, or eCommerce, which was compiled with the insight from some very helpful cloud engineers and security specialists.
According to their professional opinions, these are the applications you should turn to if you wish to keep your cloud and container secured.
1. PingSafe

PingSafe is a Cloud-native Application Protection Platform (CNAPP) that combines the powers of CSPM, CWPP, KSPM, IaC scanning, and real-time cloud detection and response. With support for AWS, GCP, Azure, and Digital Ocean, this cloud-agnostic and agentless platform provides comprehensive protection against potential cloud threats, effectively addressing challenges in multi-cloud infrastructure. PingSafe’s advanced secret scanning engine identifies 800+ types of secrets and cloud credentials in code repositories, ensuring zero leakages and preventing data breaches.
Benefits
- Zero False Positives
- Easy & Agentless Onboarding
- 100% Visibility with Real-Time Monitoring
- Offensive Security Engine
2. Tenable.io
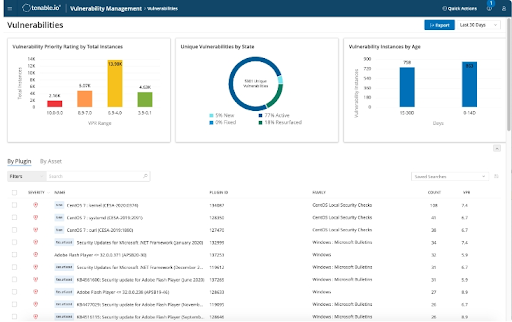
Tenable.io is a cloud-native security platform that scans all data and assets that are hosted in a virtual environment. It then performs vulnerability and risk scans to see which of these cloud-hosted assets hackers can potentially breach. It then prioritizes assets and data that are at the highest risk of a breach and guides you through the process of how to prevent it from happening.
Benefits
- Automated process that simplifies security protocols without increasing the risk of breaches
- Optimized for scalability and can sustain cloud environments that are large and complex
- Integrates with a variety of cloud platforms, including Amazon WorkSpaces alternatives
3. Qualys Container Service
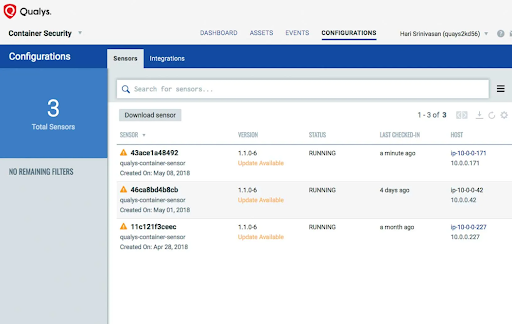
To secure your container images and detect vulnerabilities, Qualys Container Sensor helps you find the weak spots in a containerized environment. It can scan container images and run containers to detect misconfigurations that are security vulnerabilities.
Benefits
- Simplified workflow
- Continuous monitoring for vulnerabilities in containerized environments
- Multi-cloud support
4. Aqua Security

Aqua Security is a security software companies use for containers and the applications within them. It uses automated security policy enforcement and features runtime protection on top of features such as image scanning, active vulnerability detection, and a slew of other security protocols.
Benefits
- User-friendly interface
- Includes a variety of security features
- Compatible with the most popular container orchestration systems
5. Twistlock
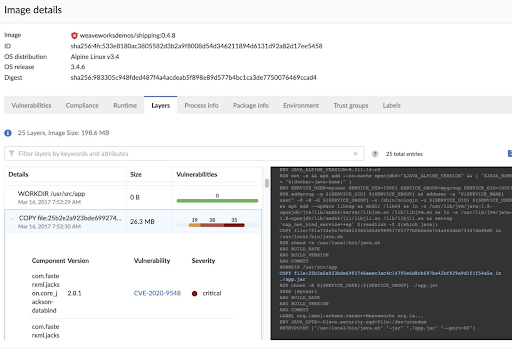
Twistlock is great for monitoring your containerized environments for security vulnerabilities. It keeps track of the network traffic and analyzes it to find risks. It manages several security aspects of your container applications to ensure security from the initial build phase all the way into production, on one convenient platform.
Benefits
- Simple and comprehensive vulnerability reports
- Complete dev-to-production security
- Runtime protection that detects suspicious activity
6. NeuVector

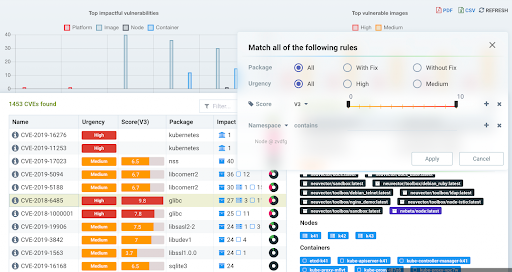
NeuVector is a container security solution that secures your applications from threats and vulnerabilities at runtime. It uses machine learning to detect both external and internal threats to the security of containerized applications.
Benefits
- Simplified management takes the edge off monitoring for vulnerabilities
- Integrates easily with DevOps workflows to ensure end-to-end app security
- Machine learning allows for advanced threat detection that pinpoints vulnerable points in container security before they can be breached
7. CoreOS Clair
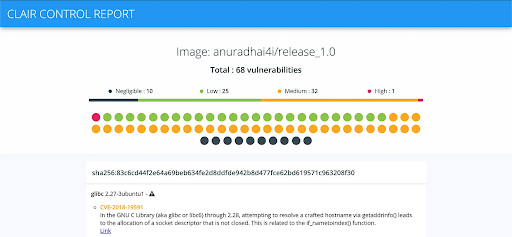
Development and security teams can use CoreOS Clair to actively monitor the vulnerabilities of containerized environments. Companies can integrate it with container orchestration platforms to regularly scan container images that are in use or being updated.
It identifies and mitigates security vulnerabilities in containerized environments in advance to help security teams deal with possible breaches.
Benefits
- Centralized vulnerability management that relays all potential risks, making it easier for security teams to prioritize which vulnerabilities to mitigate
- Highly customizable thanks to being an open-source software that security teams can tweak accordingly
- Warns of imminent threats and prevents break-ins before they happen, helping companies cut down on costs for security maintenance
8. WhiteHat Security

WhiteHat Security is an application that protects the data, assets, and software hosted on a cloud. It comes with a slew of features to help companies identify risks in the security protocol of their cloud infrastructure, which makes it a valuable asset to improving your cloud security.
Benefits
- End-to-end security keeps cloud-based applications safe from the start of development to the production stages
- On top of vulnerability scanning, it also performs penetration tests that to find cloud assets at risk of breach
- It guides security and development teams through the process of mitigating vulnerabilities in the cloud’s infrastructure
Conclusion
These 7 application security solutions are just a few of the cloud and container-based security applications that can help keep your data, applications, and valuable assets safe. While many of them seem to perform similar functions, it’s important to note that they do have nuances that make them specialized for certain use cases.
Since there is no “one-size-fits-all” solution to cloud or container security, consider your IT environments and what kind of security they need before making a final decision.
However, even with the very best toolkit you can choose, you should pay special attention to educating your team to understand security measures and improve the current policies and guidelines. This way you will reduce the potential for human error to a minimum, and include your employees in enhancing the cloud and container security on a regular basis.