To sign up for our daily email newsletter, CLICK HERE
Phishing, while considered an age-old threat, remains a much-used cybercriminal tactic to lure in victims and line their pockets as much as they can. It (specifically spear-phishing) is also a handy mechanism for threat actors that want to get into their target networks. And so, even after decades now, many individuals and organizations still get taken in by phishers. An example would be several banking and financial institutions in Italy reported on 29 March 2021.
A list of 149 IP addresses that serve as indicators of compromise (IoCs) for this particular phishing campaign was analyzed to show how a bulk IP geolocation tool like https://ip-geolocation.whoisxmlapi.com/bulk-gui can help users avoid becoming the next victims.
Analysis and Findings
The bulk IP geolocation lookup provided more details about the IP addresses on IBM’s list, including their respective source countries, regions, cities, latitude and longitude coordinates, postal codes, GeoNames IDs, time zones, Internet service providers (ISPs), domain resolutions (maximum of five per address), Autonomous System (AS) numbers, AS routes, AS domains, and AS types.
From the data obtained, we found that a majority of the malicious IP addresses (107 or 72%) traced their origins to the U.S. The remaining 42 addresses (28%), meanwhile, are scattered across 13 other countries, namely, Italy, the Netherlands, the U.K., France, Singapore, Iceland, Lithuania, Bulgaria, Germany, Denmark, Japan, Russia, and Ukraine. The chart below shows the exact number of IP addresses per country.
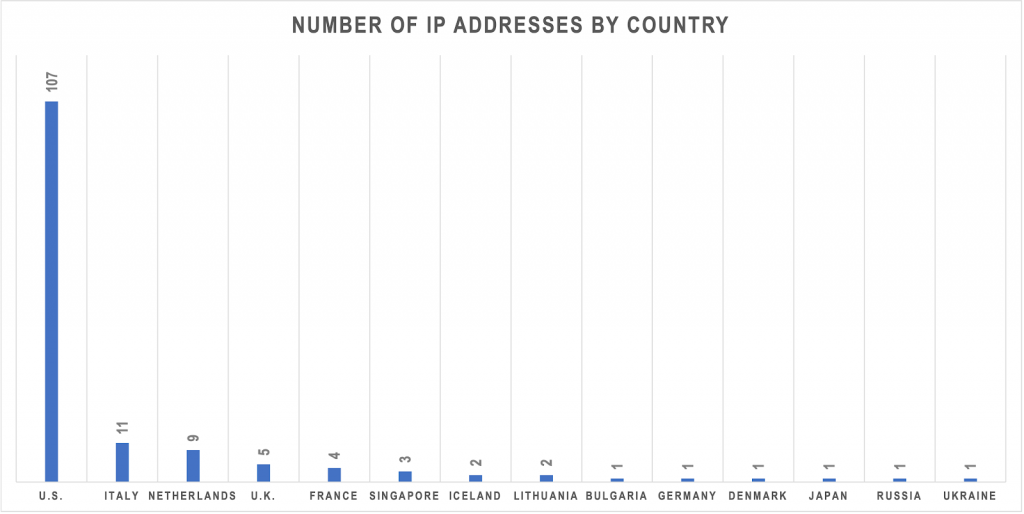
Chart 1: Country distribution of related IP addresses
We also found that most of the IP addresses (63 or 42%) were managed by Web-hosting.com. The remaining 86 addresses (58%), on the other hand, were distributed among 22 other ISPs. The rest of the top 5 are NameCheap, Inc. (34 addresses or 23%), Hostinger International Limited (11 addresses or 13%), Aruba S.p.A. Network (10 addresses or 7%), and GoDaddy.com, LLC (6 addresses or 7%). The chart below shows the rest of the ISPs responsible for the IP addresses.
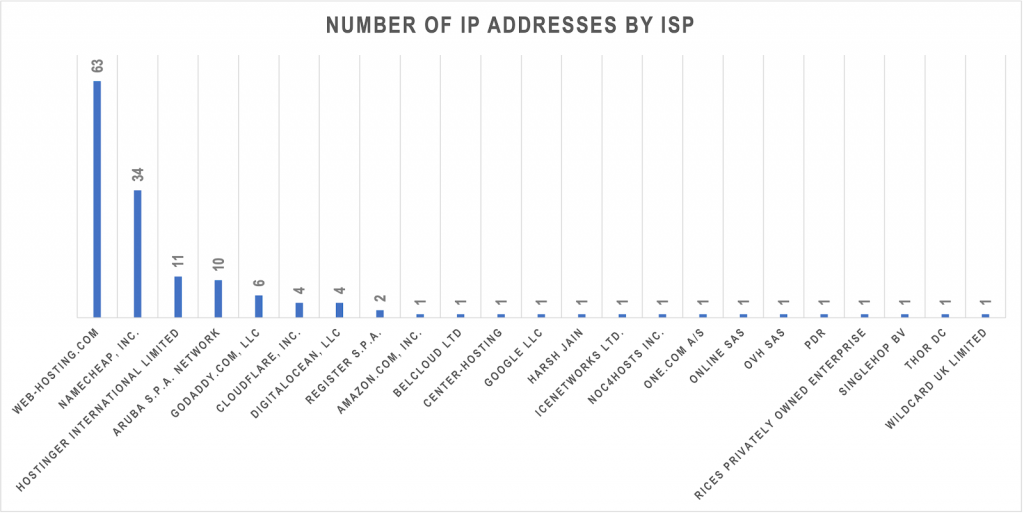
Chart 2: ISP distribution of related IP addresses
The bulk IP geolocation query also provided lists of domain resolutions for active IP addresses. An analysis of the IP-to-domain resolution volume for each address limited to five domains gave us a list of at least 541 connected domain names. See their distribution details below.

Chart 3: IP-to-domain resolution volume distribution
Using the findings above, we compiled our insights and conclusions in the next section.
Possible Security Interpretations
Not all organizations have huge security teams, which can cause alert fatigue. They need a way to prioritize alerts. In this particular attack’s case, analysts can consider paying closer attention to IP addresses associated with the countries and ISPs mentioned earlier. They can also focus first on the IP addresses that resolved to the lowest number of domains and work their way to those with the highest volume.
Companies that do not employ IP-level blocking for fear of overblocking may be able to identify the domains responsible for their hosts being tagged as malicious and block access to and from these instead. That way, they would not be in danger of blocking their customers and other stakeholders’ access along with the erring parties.
Further investigation by querying the 541 connected domains we got from the bulk IP geolocation lookup on publicly accessible threat repository VirusTotal revealed that nine were tagged “malicious” as of 5 April 2021. These resolved to the eight IP addresses (two domains shared the same IP address) marked as attack IoCs. And these IP addresses hosted at least 30 domains.
If, by any chance, your organization owns any of the domains hosted on the eight IP addresses, you may want to ask your ISP to replace your current IP address with one that does not host any malicious domain. That should prevent your website from ending up on anyone’s IP blocklist.
—–
As the deep dive into the IP addresses identified as IoCs for the phishing attack showed, bulk IP geolocation lookups can help analyze suspicious IP addresses and contribute to phishing prevention. Cybercrime has no borders after all so it is not unlikely for the same perpetrators to go after banking and financial institutions in other parts of the world using the same infrastructure.