To sign up for our daily email newsletter, CLICK HERE
While businesses have seen a flurry of activity online, there has been an increase in the number of cyberattacks. A study by the University of Maryland shows that there has been a cyberattack every 39 seconds. There has been an increase in the number of data breaches that will make the global cybersecurity spend to reach US$ 133.7 billion in 2022. These attacks not only lead to disruption of business but can also lead to hefty penalties from the government as well as a loss of consumer trust.
So, how will businesses protect their website from such attacks? Companies must imbibe stringent cybersecurity processes and procedures in place to prevent such attacks. Most medium and large-sized companies have already implemented such practices, and more companies are following suit. One of the ways to keep your website and networks protected is by installing an SSL certificate.
-
What is an SSL Certificate?
SSL is the acronym for Secure Socket Layer and is the basis for keeping the internet secure. The protocol can help to secure sensitive data that resides on the servers of the company. The communication exchange between two systems can be protected by ensuring that the data transferred between the entities is impossible to be read by an unauthorized third-party.
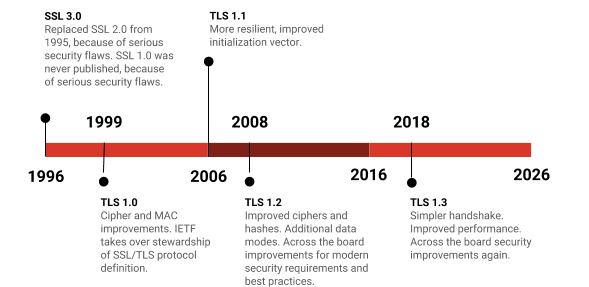
The SSL idea was developed by the well-known cryptographer – Taher Elgamal when he was the chief scientist with Netscape. It was conceived to serve as an internet-based protocol that would help secure communication over the web. The initial versions of the SSL had several flaws that led to further research to plug them. The second version released in 1995 has several weaknesses as its integrity was compromised as it used the MD5 function.
Moreover, the protocol was susceptible to truncation attacks as it relied on the TCP FIN to finish a session. The SSL v2 did not have the protection of the handshake that could lead to man-in-the-middle attacks. The third version of SSL was published in 1996 by the Internet Engineering Task Force (IETF). This version was widely in use as recently as in 2014 until few security flaws were found. There was a flaw that allowed hackers to decrypt information, like authentication cookies.
-
What are the differences between SSL and TLS?
Let us look keenly into the difference between both the protocols.
The record protocol. TLS uses HMAC after encrypting messages. It involves a secret cryptographic key and a Message Authentication Code with a hash combination and the secret key that SSL uses the MAC mechanism.
Alert messages. SSL has a “No certificate” alert message. The TLS includes several new alert messages while the alert description is removed.
The cipher suites. SSL offers support for the Fortezza cipher suite. On the other hand, the TLS protocol utilises advanced options and has a better standardization process.
The transition to TLS
The first version of the Transport Layer Security protocol (TLS) was written in 1999 and was an upgraded version of the SSL 3.0. It was written by Tim Dierks and Christopher Allen of Consensus Development. The TLS 1.0 allowed the connection to downgrade to SSL 3.0.
The future versions of TLS also came up with the TLS 1.1 being launched in 2006. It allowed for the protection against Cipher Block Chaining (CBC) attacks. It was replaced by the TLS 1.2 in 2008. It enables the hash specification and the algorithm used by the client and the server. The authenticated encryption was allowed by this version of TLS. This version also helped in verifying the length of the data based on the cipher suite.
(Source: https://www.mongodb.com/blog/post/exciting-new-security-features-in-mongodb-40)
The TLS 1.3 was developed after around 30 drafts at the IETF in the year 2018. This version has significant enhancements over the earlier versions. There was the removal of MD5 and SHA-224 support while it required digital signatures when an earlier version was used. The version also removes the RSA key exchange and requires the Perfect Forward Secrecy. The number of algorithms in the cipher suite was reduced to 2 and also directs AEAD bulk encryption.
The TLS 1.3 has removed the support of other vulnerable algorithms; viz.
- SHA-1 Hash Function
- RC4 Stream Cipher
- 3DES
- DES
- EXPORT-strength ciphers
- Various non-ephemeral Diffie-Hellman groups
Why do we call the certificates “SSL Certificates”?
We have just learnt that the SSL protocol was long debunked. The question now arises why we still refer to them as SSL certificates. The name does not matter as these certificates come from the renowned Certification Authorities who undertake a thorough authentication of the entity and the website.
The configuration of the server determines the protocols. Moreover, the CAs use the brand name as SSL certificates. Others also use the term TLS certificates, but it is the brand name that is being referred to by the CAs. You can stay assured that these certificates use the latest encryption technologies to protect communication between visitors to a website and the webserver.
Conclusion
As the number of data breaches increases over time, there is an inherent need to protect your website and prevent any data breach. One of the steps that businesses must take is to install an SSL certificate. We must notify you that these certificates use the latest encryption protocols that are currently in place. SSL was in place as the forebearers of encryption technology before being taken over by the TLS protocol. The brand name of SSL stayed, and they are still in vogue.